Colombia: A serious and transparent investigation on the instigators and perpetrators of the “Easter massacre”, the terrorist attack that in 2019 killed more than 250 people in Sri Lanka: this is what the Catholic Church asks, and through his more respected representative, Cardinal Malcom Ranjith, Archbishop of Colombo, the Church reminded the institutions of the urgent task and deepened some aspects to understand “how the April 21, 2019 attacks have occurred and who helped the aggressors”.
“We won’t hesitate in going to the street in order to protect the rights of our people”, these are the words of the Cardinal speaking in Ragama, in the north of Colombo. Despite the investigation initiated by Maithripala Sirisena, President Gotabaya Rajapaksa’s predecessor, “the procedure appears now to be lacking in transparency”, he said. “Some elements that must emerge are still hidden: who had the responsibility? Who helped the terrorists and who kept the contacts with them?” – he pointed out.
In February, the Sri Lankan government appointed a special team of six members to help the police in gathering information and accelerating a presidential investigation about the devastating attack. President Rajapaksa announced to “accelerate the ongoing investigation on the attack” that have proved to be crucial in his electoral success last November.
In fact, Rajapaksa has more than once mentioned the Easter Sunday terrorist attack during his electoral campaign in order to present himself as a “leader able to stop terrorism”. Rajapaksa won the elections against his rival Sajith Premadasa with a margin of 1.3 million votes (52.25% against 41.99% of his closest rival).
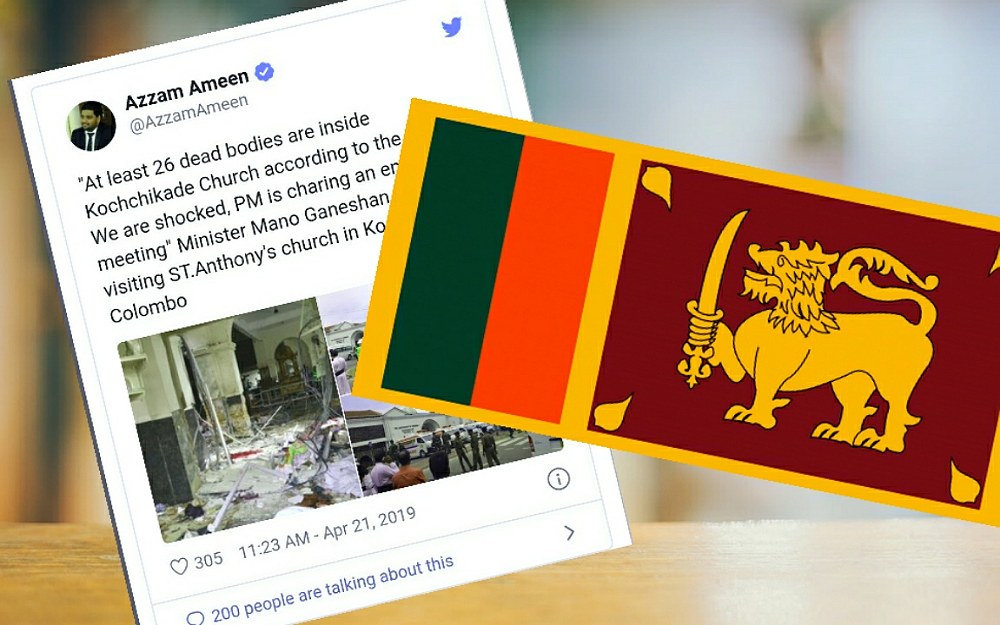
The previous government led by Maithripala Sirisena and Ranil Wickremesinghe was blamed for his incapability in preventing the attacks, even though the intelligence information had warned about the potential imminent attacks.
Nine suicide bombers belonging to the local Islamic extremist group “National Thawheed Jamaat” (NTJ) linked to ISIS carried out a series of devastating explosions that damaged three churches and the same number of luxury hotels during the Easter Sunday, killing 258 people including some foreign citizens~Agenzia Fides
Breach and Attack Stimulation
Permanent Representative of Pakistan Briefs Press on Situation in South Asia
Reporters’ Group Calls for Release of Myanmar Journalist Jailed for 5 Years
Trapper Grapples With an Alligator on the Middle of Florida Highway
Stay Alert from Scammers
35 Years On, Chinese Man Seeks Justice for ‘Stolen’ Medical College Dreams
UN Secretary-General Meets with His Special Envoy on Myanmar
Subscribe Our You Tube Channel
Fighting Fake News
Fighting Lies

















